The health app industry is rapidly growing, offering new ways to manage health. These apps track symptoms, give medication reminders, allow telemedicine, and offer real-time health monitoring. For entrepreneurs and developers, it’s important to understand data security in health apps. As an entrepreneur or developer looking to enter this dynamic market, understanding the importance of data security in health apps is crucial.
Health apps handle sensitive personal information like medical histories and health habits. This makes data security not just important but necessary. Users need to trust that their information is safe. Any breach of this trust can have serious consequences.
Moreover, health app data privacy is a growing concern. Users expect transparency about how their data is collected, used, and shared. They want control over their personal information, and meeting these expectations is essential for building trust and complying with healthcare regulations.
Related: How Innovative Health Apps Are Tackling the $4.1T Healthcare Challenge
Let’s explore essential strategies for ensuring data security in health apps. We’ll cover regulatory compliance, secure authentication, encryption, and privacy-by-design. Whether you’re an entrepreneur launching a health app or a developer building one, this article will give you insights to create secure, trustworthy apps that protect user data and follow industry standards.
Understanding Regulatory Compliance
When you’re building a health app, you need to know about the rules and regulations that govern how you handle user data. These regulations are in place to protect people’s privacy and ensure their health information is kept safe. Let’s look at some key regulations and what they mean for your app.
Key Regulations
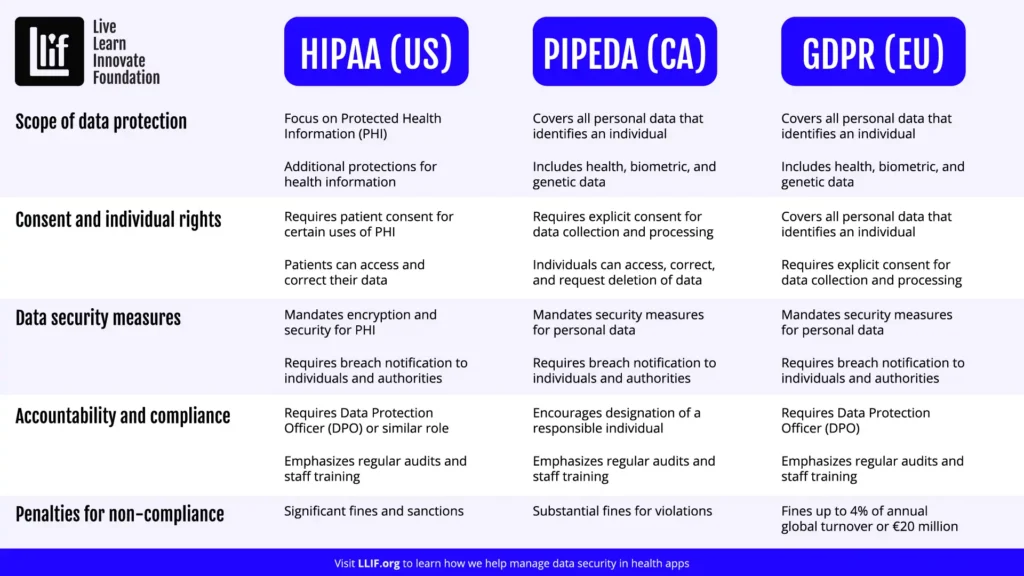
HIPAA (United States)
HIPAA, or the Health Insurance Portability and Accountability Act, is a big deal in the US. It sets the standard for protecting sensitive patient data. This extends to data security in health apps. If your app deals with any health information in the US, you’ll need to follow HIPAA rules.
GDPR (Europe)
The General Data Protection Regulation applies to any app that handles data from European users, this includes health apps. It gives people more control over their personal data and aims to simplify the regulatory environment for international business.
PIPEDA (Canada)
The Personal Information Protection and Electronic Documents Act is Canada’s main privacy law. It governs how private sector organizations collect, use, and disclose personal information. This applies to data security in health apps, too.
Compliance Requirements
To comply with these regulations, you’ll need to focus on:
Data protection measures: This includes using strong encryption, secure servers, and regular security audits.
User consent and rights: You must clearly explain how you’ll use user data and get their permission. Users should also have the right to access, correct, or delete their data.
Reporting breaches: If there’s a data breach, you need to report it to the authorities and affected users within a specific timeframe.
Consequences of Non-Compliance
Failing to comply with these regulations can have serious consequences:
Legal repercussions: You could face lawsuits from users or regulatory bodies.
Financial penalties: Fines for non-compliance can be hefty. For example, GDPR fines can be up to €20 million or 4% of global annual turnover, whichever is higher.
Loss of user trust: Perhaps the most damaging consequence is losing the trust of your users. Once trust is broken, it’s hard to regain, and it can seriously impact your app’s success.
Common Compliance Challenges for Health App Developers
- Navigating Complex Regulations: Developers must understand and comply with various regulations like HIPAA, GDPR, and PIPEDA, each with its own requirements.
- Ensuring Data Protection Measures: Implementing strong data protection strategies, including encryption and security audits, is essential to prevent breaches and ensure compliance.
- Obtaining User Consent and Managing Rights: Developers need to create clear privacy policies and consent forms, allowing users to access, correct, or delete their data.
- Reporting Data Breaches: A defined incident response plan is necessary to report breaches to authorities and affected users promptly, as delays can lead to penalties.
- Interoperability and Integration: Ensuring that health apps can securely integrate with other healthcare systems while maintaining compliance is a significant challenge.
- Keeping Up with Evolving Regulations: Developers must stay informed about changing regulations and update their compliance strategies accordingly, which can be resource-intensive.
- Balancing Security and Usability: Finding the right balance between robust security measures and a user-friendly experience is crucial for user engagement.
By addressing these challenges, developers can ensure data security in health apps that protect sensitive user data and foster trust.
Remember, complying with these regulations isn’t just about avoiding penalties. It’s about building a trustworthy app that users feel safe using. By prioritizing data security and privacy from the start, you’re setting your health app up for long-term success.
Interested in building your own health app? Check out how LLIF helps enforce data security in health apps without you having to start from scratch.
Implementing Strong Authentication Mechanisms to Ensure Data Security in Health Apps
When it comes to data security in health apps, strong authentication is your first line of defense. It’s like having a super-secure lock on your front door. Let’s dive into the types of authentication you can use and some best practices to keep your users’ data safe.
Types of Authentication
Single Sign-On (SSO) From Major Providers like Apple or Google
Using Single Sign-On (SSO) from major providers like Apple and Google can greatly benefit health app developers. Apple Sign In is particularly appealing because it prioritizes user privacy, does not track user activity, and incorporates two-factor authentication by default, making it secure and user-friendly. Additionally, it helps with compliance, especially under regulations like GDPR, as it minimizes data collection.
Similarly, Google Sign In offers a broad reach since many users already have Google accounts. It adheres to OAuth 2.0 and OpenID Connect standards, providing a reliable authentication method that is compatible across platforms. Implementing Google Sign In involves configuring the Google API Console and handling authentication responses effectively.
When integrating these SSO options, developers must ensure that health data is stored separately and securely, without direct links to the SSO provider. For highly sensitive health information, adding an extra layer of authentication beyond SSO is advisable.
Clear communication with users about how their data is protected and the limitations of the SSO provider’s access is essential. Furthermore, it’s important to ensure that using these SSO options aligns with compliance requirements while also offering users a choice of sign-in methods to enhance their experience. Overall, SSO can simplify the authentication process while providing excellent data security in health apps.
Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of data security in health apps beyond just a password. Here’s how it works:
- The user enters their username and password.
- They’re then asked for a second piece of information, like a code sent to their phone or email.
This two-step process makes it much harder for hackers to break in, even if they’ve somehow gotten the password.
Biometric Authentication
Biometric authentication uses unique physical characteristics to verify a user’s identity. The two most common types are:
- Fingerprint Recognition: Users can unlock the app by scanning their fingerprint.
- Facial Recognition: The app uses the device’s camera to verify the user’s face.
Biometrics are convenient for users and tough for hackers to fake.
Best Practices
Use of Strong, Unique Passwords
Encourage your users to create strong passwords. A good password should:
- Be at least 12 characters long
- Include a mix of uppercase and lowercase letters, numbers, and symbols
- Not be a common word or phrase
Consider using a password strength meter in your app to help users create strong passwords.
Regular Password Updates
While frequent password changes can be annoying for users, it’s a good idea to prompt updates every few months. This helps protect against password-guessing attacks.
User Education on Authentication Methods
Many users don’t understand why strong authentication is important. Include clear, simple explanations in your app about:
- Why you’re using these security measures
- How to use them correctly
- What to do if they suspect their account has been compromised
Overall, the goal is to make your app secure without making it frustrating to use. Balancing security and user experience is key. By implementing these strong authentication mechanisms and following these best practices, you’ll be well on your way to creating a health app that users can trust with their sensitive information.
De-Identification to Enforce Data Security in Health Apps
De-identification of data is a crucial process in healthcare to protect patient privacy while still allowing valuable data to be used for research and analysis. It’s process of removing or obscuring personal health information in medical records to protect patient privacy. It aims to prevent a person’s identity from being connected with their health information.
De-identification enables sharing of data for secondary research purposes like public health studies while meeting privacy regulations such as HIPAA. It balances the need for data utility with privacy protection.
Common de-identification methods include:
- Suppression: Removing identifiers like names and addresses
- Generalization: Reducing specificity of data (e.g. using age ranges instead of exact ages)
- Perturbation: Adding noise to data
- Synthetic data generation: Creating artificial data with similar statistical properties
The HIPAA Privacy Rule defines 18 categories of Protected Health Information identifiers that must be removed or obscured to achieve de-identified status. Perfect de-identification is difficult to achieve. There’s often a trade-off between data utility and privacy risk that must be evaluated case-by-case.
Various de-identification software tools are available to automate the process, including:
- iMerit Ango Hub
- Google Healthcare API
- AWS Comprehend Medical
- IBM InfoSphere
- Microsoft’s de-identification service in Azure Health Data Services
De-identification allows for sharing data for research and public health initiatives while enabling data marketplaces and exchanges and improving overall research efficiency. Emerging privacy-enhancing computation methods like federated learning and differential privacy offer complementary approaches to traditional de-identification.
By implementing de-identification practices, health apps can unlock the value of their data for research and innovation while maintaining patient trust and regulatory compliance.
Encryption to Enforce Data Security in Health Apps
When you’re dealing with sensitive health data, encryption is like a secret code that keeps information safe from prying eyes. Let’s break down the key aspects of data encryption for your health app.
Encryption Methods
There are two main times when you need to protect data: when it’s moving and when it’s sitting still.
- Encryption in transit (SSL/TLS): This is like putting your data in an armored truck as it travels across the internet. SSL (Secure Sockets Layer) and its more modern version, TLS (Transport Layer Security), create a secure tunnel for data to move through. When you see “https” in a web address, that’s SSL/TLS at work.
- Encryption at rest (AES-256): This protects data when it’s stored on a device or server. AES-256 is a super strong encryption method that’s widely used. It’s like locking your data in a vault that’s nearly impossible to crack.
Implementation Strategies
To make sure your encryption is rock-solid, consider these strategies:
- End-to-end encryption: This means data is encrypted from the moment it leaves the user’s device until it reaches its final destination. No one in between, not even your app’s servers, can read the data.
- Secure key management: Encryption keys are like the passwords to your encrypted data. Keep these keys super safe, rotate them regularly, and never store them in the same place as the data they protect.
Benefits of Encryption
Why go through all this trouble? Here are the big payoffs:
- Protection against data breaches: Even if someone manages to steal your data, they won’t be able to read it without the encryption keys. It’s like a thief stealing a safe but not knowing the combination.
- Compliance with regulations: Many health data regulations, like HIPAA, require encryption. By implementing strong encryption, you’re already on your way to meeting these requirements.
Keep in mind encryption isn’t just a technical feature – it’s a promise to your users that you’re serious about protecting their health information. By using strong encryption methods and implementing them carefully, you’re building trust and safeguarding your app’s most valuable asset: user data.
Ensuring User Consent and Transparency
In the world of health apps, trust is everything. Users need to know that you’re handling their sensitive health information responsibly. This is a cornerstone for data security in health apps. Let’s dive into how you can ensure user consent and maintain transparency.
User Consent
Getting user consent isn’t just a legal requirement – it’s about respecting your users and building trust. Here’s how to do it right:
Clear Communication About Data Usage
Don’t bury important information in long, complicated terms of service. Instead, use simple language to explain what data you’re collecting and why. For example, you might say, “We collect your heart rate data to provide personalized exercise recommendations.”
Obtaining Explicit Consent
Make sure users actively agree to your data practices. This could be a checkbox they need to tick or a clear “I agree” button. Avoid pre-ticked boxes or assuming consent – that’s a big no-no in most regulations.
Transparency Measures
Being transparent about your data practices helps users feel in control and builds long-term trust. Here’s how to keep things open and honest:
Privacy Policies
Your privacy policy should be easy to find and understand. Break it down into sections, use plain language, and maybe even add some visuals to make it more digestible. Remember, the goal is for users to actually read and understand it, not just scroll past.
Data Usage Notifications
Keep users in the loop about how their data is being used. If you’re introducing a new feature that uses their data differently, let them know. For example, “We’ve added a new feature that analyzes your sleep patterns to suggest better bedtime routines. You can turn this on in your settings.”
User Control Over Data Sharing
Give users the power to decide what data they share. This could mean granular permissions (like allowing access to step count but not heart rate) or the ability to opt out of certain data uses. Make these controls easy to find and use within your app.Remember, transparency isn’t just about following rules – it’s about building a relationship with your users. By being open and honest about how you handle data, you’re showing users that you respect their privacy and value their trust. This can set your health app apart in a crowded market and lead to more loyal, engaged users in the long run.
Secure Cloud Infrastructure for Data Security in Health Apps
As health apps increasingly rely on cloud services for data storage and processing, ensuring a secure cloud infrastructure becomes paramount. Let’s explore how to choose the right cloud provider and implement essential security measures.
Reputable, Compliant providers
When dealing with health data, it’s essential to choose a cloud provider that complies with HIPAA (Health Insurance Portability and Accountability Act) regulations. Providers like Amazon Web Services (AWS), Google Cloud, and Microsoft Azure offer HIPAA-compliant services and have a track record of reliability and security.
Related: Unlock Health App Development: Make Specialty Care Apps With LLIF
Data center security certifications
Look for providers with recognized security certifications, such as ISO 27001, SOC 2, and HITRUST. These certifications indicate that the provider follows stringent security standards and best practices for data protection.
Cloud Security Measures
Once you’ve chosen a reputable provider, implementing robust security measures is crucial to protect health data stored in the cloud.
Data encryption
Ensure that all data stored in the cloud is encrypted both in transit and at rest. Use strong encryption standards like AES-256 for data at rest and SSL/TLS for data in transit. This ensures that even if data is intercepted or accessed without authorization, it remains unreadable.
Access controls
Implement strict access controls to limit who can access sensitive health data. Use role-based access control (RBAC) to assign permissions based on user roles and responsibilities. Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide two or more verification factors.
Regular Audits
Regular security assessments and compliance checks are essential to maintain a secure cloud infrastructure and ensure ongoing compliance with regulations.
Security assessments
Conduct regular security assessments to identify and address vulnerabilities in your cloud infrastructure. This includes penetration testing, vulnerability scanning, and security audits. Regular assessments help you stay ahead of potential threats and ensure that your security measures are effective.
Compliance checks
Perform periodic compliance checks to ensure that your cloud infrastructure continues to meet regulatory requirements. This includes reviewing security policies, procedures, and controls to ensure they align with HIPAA and other relevant regulations. Compliance checks help you identify and address any gaps in your security posture.
Choosing a reputable, HIPAA-compliant cloud provider and implementing robust security measures are essential steps in data security in health apps. By encrypting data, enforcing strict access controls, and conducting regular security assessments and compliance checks, you can build a secure cloud infrastructure that protects sensitive health information and maintains user trust.
Data Security in Health Apps by Using Privacy by Design
Privacy by Design is a proactive approach to protecting user data. Instead of treating privacy as an afterthought, it makes privacy an essential component of your app from the very beginning. Let’s explore how to implement this approach in your health app development.
Proactive not reactive
Don’t wait for privacy breaches to happen. Anticipate and prevent privacy-invasive events before they occur. This means thinking about potential privacy issues at every stage of development.
Privacy as the default setting
Make privacy the standard setting. Users shouldn’t have to take extra steps to protect their privacy – it should be built into the system by default. For example, data sharing should be opt-in rather than opt-out.
End-to-end security
Ensure that all data is securely collected, used, retained, and destroyed. This means implementing strong security measures throughout the entire lifecycle of the data.
Implementation in Development
Integrating privacy from the start
From the moment you start sketching out your app idea, consider privacy implications. As you develop features, always ask, “How does this impact user privacy?” This approach helps you catch potential issues early when they’re easier and cheaper to fix.Regular privacy impact assessments
Conduct privacy impact assessments at key stages of development. These assessments help you identify and mitigate privacy risks. They should cover questions like:
- What personal data are we collecting?
- Is this data necessary for the app’s function?
- How are we protecting this data?
- What are the potential risks to user privacy?
Benefits
Enhanced user trust
When users see that privacy is a core feature of your app, not just an add-on, they’re more likely to trust you with their sensitive health data. This can lead to higher user retention and positive word-of-mouth recommendations.Long-term data protection
By building privacy into your app from the ground up, you’re setting yourself up for long-term success. It’s much easier to maintain strong privacy practices when they’re an integral part of your app’s architecture.
Practical Tips for Implementation
- Use data minimization: Only collect the data you absolutely need.
- Implement privacy-enhancing technologies: Use techniques like differential privacy to protect individual user data while still allowing for useful analysis.
- Provide clear privacy controls: Make it easy for users to understand and control their privacy settings.
- Regular training: Ensure your development team understands the importance of privacy and stays up-to-date on best practices.
Remember, Privacy by Design isn’t just about compliance – it’s about building trust with your users and creating a health app that respects and protects their personal information. By making privacy a fundamental part of your app’s design, you’re not just following best practices – you’re setting your app apart in a market where privacy is increasingly valued by users.
Conclusion
We’ve looked at some key strategies for keeping data secure in health apps. We talked about the importance of following regulations, using strong authentication methods, and employing effective data encryption techniques. Additionally, we emphasized the necessity of obtaining clear user consent and being transparent about data usage. We also covered the significance of having a secure cloud infrastructure and adhering to the principles of Privacy by Design. By now, you should have a solid grasp of what it takes to protect data in your health apps..
Prioritizing data security in health apps is not just about meeting legal requirements; it’s about building trust with your users and protecting their sensitive health information. As you develop your health app, adopting these best practices will help you create a secure, reliable, and user-friendly product that stands out in the market.
FAQ
What are the key regulations for health app data security?
- Answer: Regulations such as HIPAA (US), GDPR (Europe), and PIPEDA (Canada) set stringent standards for protecting patient health information.
How can I ensure my health app is secure?
- Answer: Implement strong authentication mechanisms, encrypt data, ensure user consent and transparency, keep the app updated, train employees, use secure cloud infrastructure, and have an incident response plan in place.
What is “privacy by design”?
- Answer: “Privacy by design” involves integrating privacy measures into the app’s architecture from the outset, ensuring data protection throughout its lifecycle.
Why is regular updating important for health apps?
- Answer: Regular updates help prevent exploitation of known vulnerabilities, ensuring the app remains secure against potential threats.